As the seasons shift, so too do the tactics of cybercriminals. They have an entire tree of malware types to pick from—each designed to steal data, take control, and wreak havoc on your system. Like autumn leaves falling unpredictably, malware attacks come in different forms, each requiring unique strategies to combat.
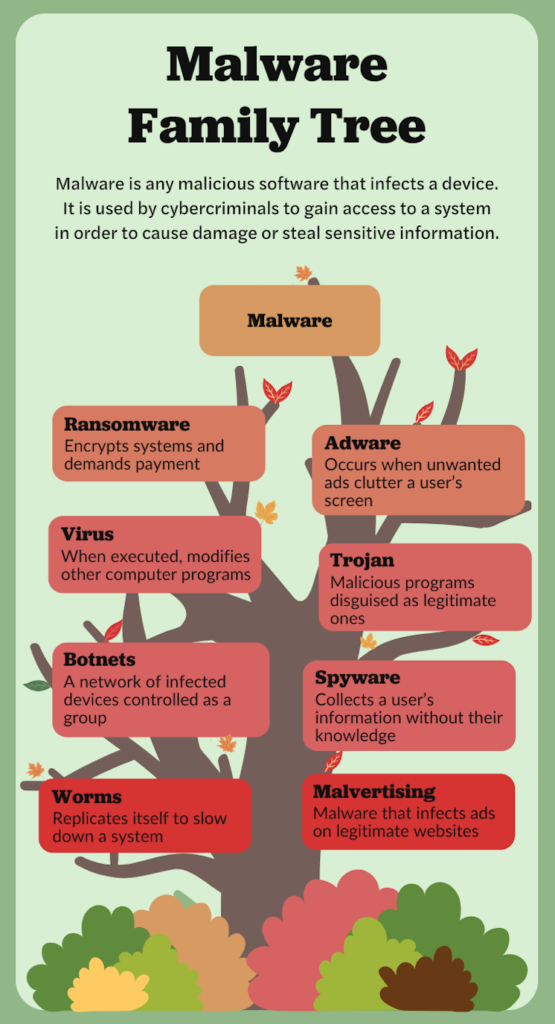
Understanding the various types of malware is crucial, as each operates differently and demands specific defenses. Let’s take a look at the different threats lurking in the digital forest:
- Self-Spreading Malware – Some malware acts like an invasive species, spreading independently without any user interaction. Worms, for example, replicate themselves across networks, infecting multiple systems without needing a host file. The best defense? Strong network security, up-to-date software, and proactive monitoring.
- Ransomware – This is the equivalent of a hijacked harvest. Ransomware locks down your files and demands payment for their release. Once it takes root, it can be difficult to remove without backups. A solid defense includes frequent data backups, email filtering, and employee awareness training to avoid phishing scams.
- Spyware – Lurking like a silent observer in the underbrush, spyware secretly monitors your activity, collecting sensitive information such as login credentials and financial data. Anti-malware software, strong passwords, and multi-factor authentication can help keep your information out of the wrong hands.
- Adware – Software designed to display online advertisements, often in the form of pop-ups, banners, or redirects, and can be unwanted or malicious.
- Trojan – A Trojan horse, or simply a Trojan, is a type of malware disguised as legitimate software, designed to deceive users into installing and running it, potentially granting attackers access to a system for malicious purposes.
- Botnets – A group of computers that have been infected by malware and have come under the control of a malicious actor. The term botnet is a portmanteau from the words robot and network and each infected device is called a bot..
- Worms – A type of malware that can automatically propagate or self-replicate without human interaction, enabling its spread to other computers across a network. A worm often uses the victim organization’s internet or a local area network (LAN) connection to spread itself.
- The Ever-Growing Threat Landscape – These are just a few examples of the many types of malware cybercriminals use. Read more.
Stay Secure with BlueCore Technologies
At BlueCore Technologies, we stay ahead of the cybercriminals, adapting security solutions to combat evolving threats. Our comprehensive cybersecurity strategies ensure that your business remains protected, no matter what season of cyber threats comes your way.
Don’t wait until an attack happens—take proactive steps to secure your digital environment today! Contact BlueCore Technologies for a consultation and let’s fortify your cybersecurity defenses together.
Join us in transforming your IT experience. Learn more about us on our website or contact us today to get started:
Call: (615) 807-1266
Email: [email protected]
